Overview:
The traditional perimeter is dead — users, data, and workloads are now everywhere. Cloud adoption, hybrid work, and sophisticated threats have rendered legacy security models ineffective. Zero Trust is the new security paradigm: “Never trust, always verify.”
At Symosis, we help organizations design, implement, and operationalize Zero Trust Architectures that are scalable, compliant, and rooted in strong identity principles. Whether you’re securing a public cloud, SaaS ecosystem, or legacy enterprise infrastructure, we tailor Zero Trust to fit your business, risk profile, and technology stack.
Common Challenges in Adopting Zero Trust
🚧 Fragmented Identity Systems
Multiple identity providers and directories across cloud, SaaS, and on-prem apps can’t provide unified access control or auditability.
🚧 Lack of Visibility into User and Device Behavior
Most organizations struggle to detect risky identity activity, compromised credentials, or lateral movement in real-time.
🚧 Privilege Creep and Overprovisioned Access
Without lifecycle controls, users accumulate excessive permissions, violating least-privilege principles and increasing breach impact.
🚧 Legacy Networks and Flat Architecture
Traditional networks lack segmentation, enabling threat actors to move freely once inside.
🚧 Compliance & Audit Pressures
New mandates from CISA, FedRAMP, and EO 14028 demand zero trust maturity, but many organizations lack a roadmap.
How Symosis Helps
We guide clients from strategy through execution. Our Zero Trust services are built around:
-
Identity as the New Perimeter
We focus on IAM, PAM, and device trust to replace outdated perimeter-based models. -
Modular Architecture
We deploy Zero Trust in phases, prioritizing quick wins (like identity federation, MFA, or segmentation) without disrupting operations. -
Tool Rationalization
We help unify your existing tools (Entra ID, CrowdStrike, Duo, etc.) into an integrated Zero Trust control plane. -
Compliance Alignment
We map Zero Trust efforts to regulatory frameworks like NIST 800-207, CISA ZTMM, HIPAA, and SOC 2. -
Vendor-Agnostic Expertise
Symosis works across Microsoft, AWS, Google, SentinelOne, Palo Alto, and more — ensuring the right fit for your environment.

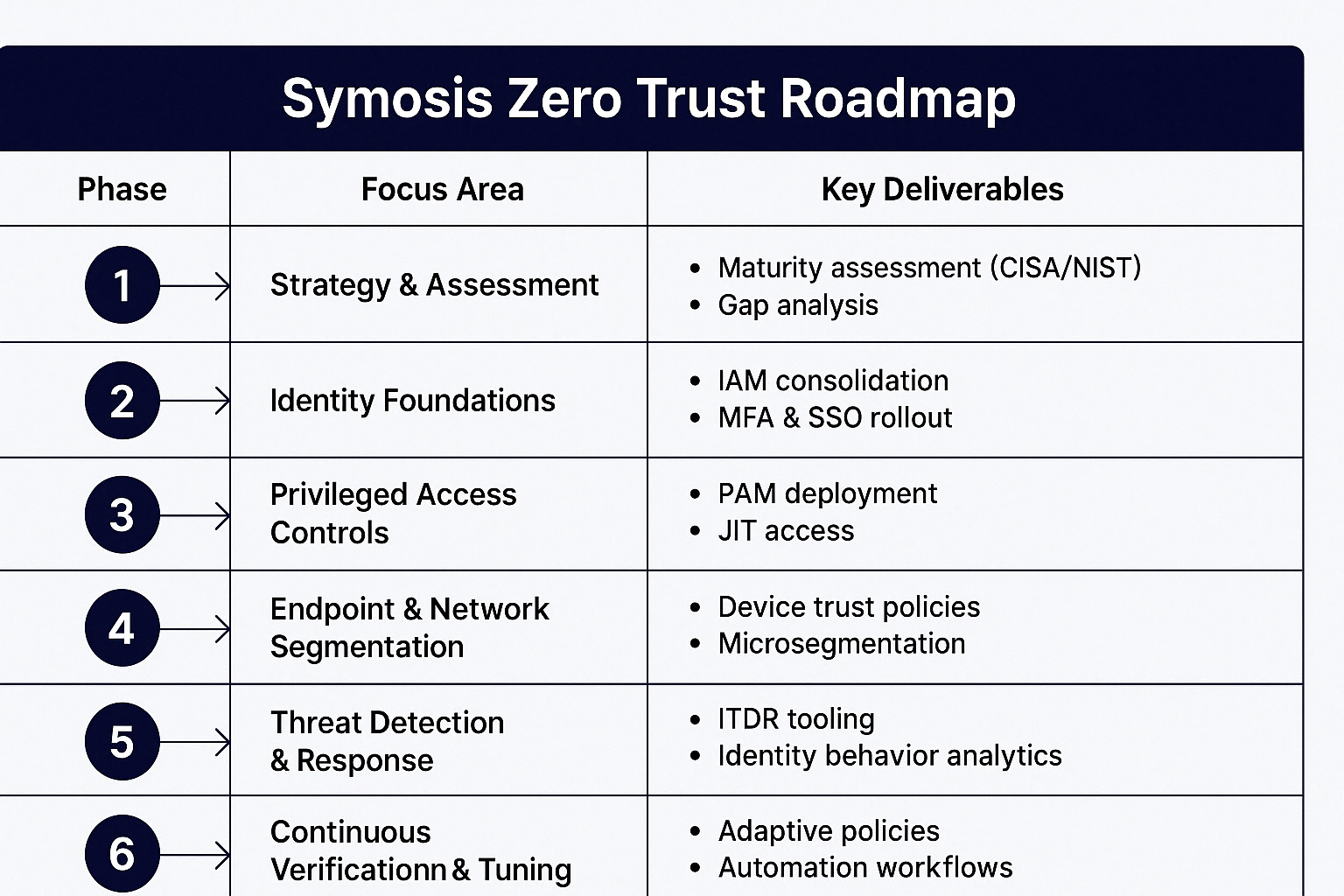
What We Deliver:
- Zero Trust Strategy & Implementation (NIST 800-207, CISA ZTMM)
- Identity & Access Management (IAM) – RBAC, SSO, lifecycle automation
- Privileged Access Management (PAM) – vaulting, session control, JIT access
- Endpoint & Network Segmentation
- Identity Threat Detection & Response (ITDR)
Outcomes:
- Reduced credential abuse and lateral movement
- Compliance with Zero Trust mandates (FedRAMP, DoD)
- Full visibility and control across identities, assets, and sessions
